Kerberos User Pass-through is the recommended authentication method for Conquest III, configured as follows:
1. Make sure that the Date and Time of all servers and workstations involved in Kerberos Delegation, are synchronised.
2. Use the ‘Active Directory Users and Computers’ tool to ensure that all AD User Accounts of Conquest Users are not marked ‘Sensitive and cannot be delegated’.
3. Most of the Service Principal Names (SPNs) required to set up Kerberos for Conquest III will already be available per server, set when their Roles and Features were configured. For exceptions use the SETSPN command to create them. See Set Service Principal Names for details
4. Here is an example list of servers that could work together with Kerberos Delegation:
•Firewall Server X does not usually provide any services to other computers
•Web Server A provides ‘http’
•SQL Server B provides SQL Server - Database
•SQL Server Y provides SQL Server - Other Application Database
•Reporting Services Server C provides SQL Server - Reporting Services and ‘http’
•File Server D provides its File System e.g. for Document the Conquest Document Directory
•File Server E provides its File System e.g. for icons and images
•File Server F provides its File System e.g. for directly pathed Documents created by Conquest II
5. Use the ‘Active Directory Users and Computers’ tool, Delegation Tab, to delegate services:
•Firewall Server X delegates Web Server A to provide its ‘http’ service
•Web Server A delegates:
•SQL Server B to provide its Database service
•SQL Server Y to provide its Database service (for integration)
•SQL Reporting Services Server C to provide its Reporting service
•Reporting Services Server C to provide its ‘http’ service
•File Server D to provide its ‘Cifs’ service for the Document Directory
•File Server E to provide its ‘Cifs’ service for Icons
•File Server F to provide its ‘Cifs’ service for directly pathed Documents
•SQL Server B delegates Reporting Services Server C to provide SQL Reporting Services and ‘http’
•Reporting Services Server C Delegates SQL Server B to provide SQL Server for the Conquest database
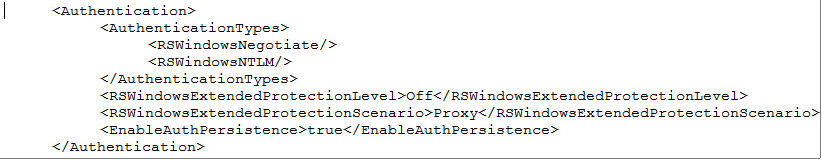
6. Microsoft Reporting Services does not default to use Kerberos:
•To make sure that Windows “Negotiate” Authentication Type is enabled, on the Server hosting Reporting Services edit the RSReportServer.config file
•In the ‘AuthenticationTypes’ section put <RSWindowsNegotiate/> above <RSWindowsNTLM/>

7. Restart the SQL Server service that hosts the database and, if separate, that hosts Reporting Services
Examples of Delegation:
•In this example a firewall server Delegates the ‘https’ Service and some web site URLs from Web Servers:
•In this example a Web Server Delegates:
•‘cifs’ file service on some file servers
•‘http Report.conquest-solutions.com.au’ Service for access to an instance of Reporting Services
•‘http Report2.conquest-solutions.com.au’ Service for access to an instance of Reporting Services
•The SQL Server Services on “V-KATICH” for data
Things to be aware of:
•Open Delegation is known to have problems, especially on a big AD, where propagation failure might be an issue. Specified Delegation is non-fail, in our experience, with the added benefit of letting the administrator know exactly what services are being used
•If a SQL Server instance is running under a Service Account, the Delegation will be to services from that account, not from the machine
•Make sure that the web browsers of workstations for Conquest III have been configured, so that the Conquest URL is a trusted site on the Local Intranet. See Client Workstation, for more details
•Changing any part of the SQL Server delegation by the Web Server must be followed with a Restart of the SQL Server instance
•Kerberos protocol applies inside a Domain Network, stopping at the perimeter Firewall
•The ‘Document Directory’ System Option is the root path to files that are attached to Conquest Data Objects (Assets, Actions etc). However, Conquest II was also able to access files from outside of the ‘Document Directory’. There are two ways of dealing with this:
•Move directly pathed files, into the ‘Document Directory’ path or sub-folders then use SQL to modify the document tables to match. Conquest Support staff can assist you with this
•Leave the existing files where they are, and give access to them with Delegations, as described in 5 above