When Conquest 3 is installed, the Web Site uses ‘Application User (pass-through authentication)’ by default. This form of authentication uses the Kerberos protocol and is recommended by Conquest Software because it:
•Improves security of the data used by Conquest 3 inside the network
•Meets the requirements of Customers using third party applications needing individual User Accounts to identify data from Conquest
•Has advantages as follows:
•It is a newer technology than NT LAN Manager (NTLM)
•Is Faster than NTLM
•Uses Mutual Authentication – client to service/service to client
•Is Open Standard
•Uses Delegated Services to decrease the opportunity for misuse/mischief.
•Is Smart card logon capable, which protects passwords
Before installing Conquest 3 for the first time, set up the servers hosting it, to use Kerberos Authentication. Although the initial set up in Active Directory is complex, once done it will rarely need changing. See the Kerberos Delegation section for details.
Once Kerberos Authentication is set up, it will persist and will allow future Conquest 3 versions to be installed and run “out of the box” on the same Web Server, with no further configuration, until such time as the Active Directory Servers involved with Conquest 3 are significantly reconfigured.
The Active Directory administrator must be able to configure the following:
•Active Directory for Application User (Pass-through authentication)
•The Public Firewall, if Conquest 3 is to have public access
•IIS
•SQL Server connection
•SQL Server Reporting Services
To configure pass-through authentication:
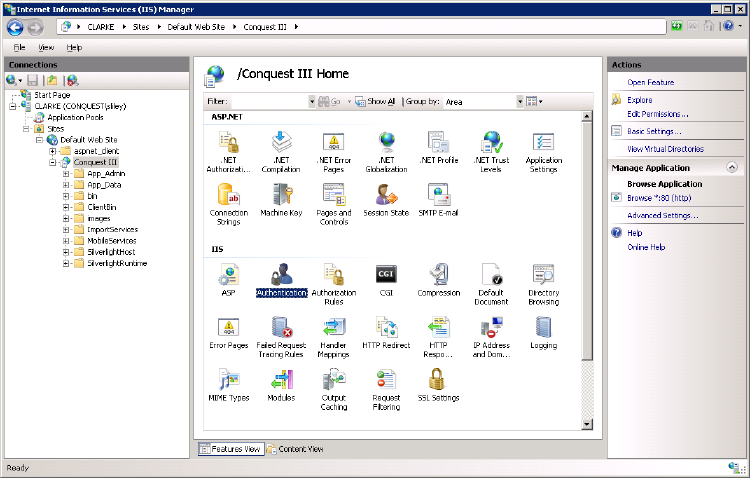
Step 1. Select the Conquest 3 instance then open the Authentication Feature, which shows the Authentication options.

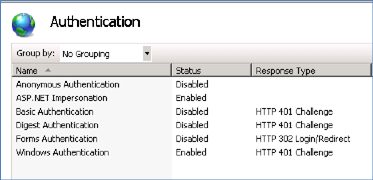
Step 2. Double-click on the “Windows Authentication” option to see the Authentications. This image shows them as set by the Conquest 3 Installer.
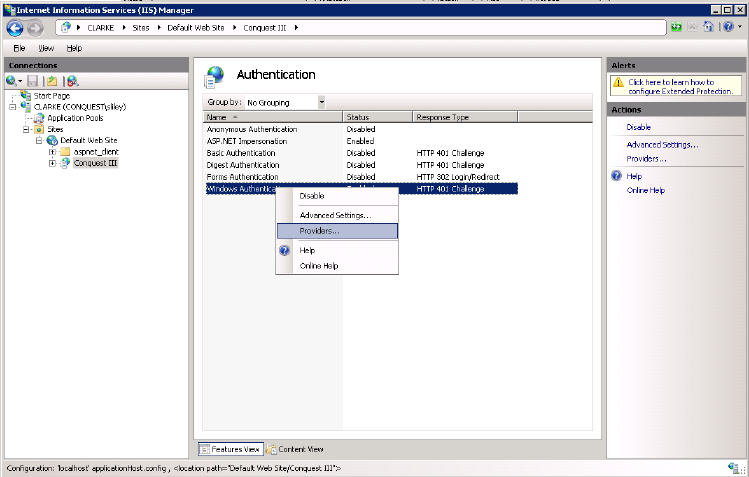
Step 3. Right-click on the “Windows Authentication” option and from the Drop-list select the “Providers…” option:
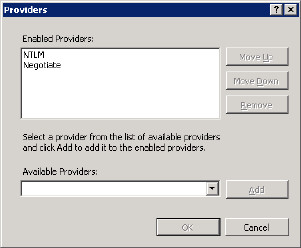
The NTLM option must be at the top of the list. If it isn’t, select it and use the Move Up button until it is.
If Application User Pass-through authentication is not required then Service Account Authentication must be used